Lei Feng Network (search "Lei Feng Net" public concern) : not only the first bank in Taiwan by cross-border hacking, cross-border hacking ATMs across the region, infiltration of more than 100 banks, at least 30 countries and regions The amount of money stolen was about 300 million U.S. dollars, and so far the case has not been broken. So, how did hackers attack? This article attempts to restore the entire incident process, the author of 360 team chase the day.

In mid-July of 2016, 41 ATMs from more than 20 branches of Taiwan’s Taiwan Bank’s Taiwan branch were hacked and stolen more than NT$82.27 million. At present, the case has been uncovered, and criminal suspects were captured and recovered. Part of the stolen money. The 360 ​​Sun chasing team analyzed the hacker attack theft against the ATM machine, restored the entire incident process, analyzed the hacker attack techniques and procedures, and provided security recommendations accordingly.
| Event ProcessTaiwan’s First Bank’s First Bank (First Bank) is a large commercial bank in the Taiwan region of China (hereinafter referred to as Taiwan). The Bank launched a cardless cash withdrawal service in early June. (The following sections are taken from public reports from Taiwan media)
July 11, 2016:
The police in Taiwan received a report from the public and said that they saw people acting weird when they operated the ATM, and the ATM had unclear instructions.
July 12, 2016:
The first bank issued an announcement that "The first bank ATM was abnormally pirating the rights of its customers will not be affected." It said that "the ATMs of the first bank branch were abnormally stolen, and the committing process took about 5 to 10 minutes. The transaction focused on July 9. On July 10 and July 10, the total amount of stolen money in this case was about NT$70 million, and there were anomalies in 34 ATMs in 20 branches, and the alarms were handled urgently. Execution of banknotes is the same model (pro cash1500 model) of Wincor (Wincor) company. At present, this model has been completely suspended. "Wincor's products involve the banking and retail industry, In the banking industry, it includes cash self-service equipment and non-cash self-service terminals and solutions. It represents hardware products such as automatic teller machines, deposit and withdrawal machines, multimedia service terminals, passbook printers, etc., and operates in more than 130 countries and regions. . In this Taiwanese robbery, the ATMs attacked by gangsters are actually old models, which can be purchased for as long as $1,475 at the ebay auction site.
After being cleared and verified by the First Bank, a total of 41 ATMs were stolen and the amount stolen was more than 83.27 million yuan. This is the first bank in Taiwan to be cross-border hacking.
July 17, 2016:
Taiwan’s police informed that it had locked 16 suspects and 1 per capita from the outside by means of surveillance videos, etc. 13 of them had left Taiwan and captured the main criminal Latvian man Andrew in Ilan on the 17th. Taipei arrested one Romanian and Moldovan accomplice and recovered 60.50 million yuan. According to the investigation, the suspects entered Taiwan in batches from Turkey, Hong Kong and other places in the name of tourism from July 6th to Taipei, New Taipei City and Taichung City from January 9 to 11. A group of people uses the Trojan horse program to invade the first bank ATM, and then automatically uses the communication software to remotely control the ATM to automatically vouch for money. The rest of the associates are responsible for the money and the style. After committing the crime, 13 suspects quickly left Taiwan. The 60.5 million cash notes that were recovered were stored at Taipei Station. The suspects deposited some of their cash in the form of a “dead bag†by means of a “dead dropâ€. On the evening of the 17th, the Taiwan authorities’ “policy administrator†Chen Guoen said that cross-border hackers invaded ATMs across the country, infiltrated more than 100 banks, and at least 30 countries and regions suffered losses. The amount stolen was approximately 300 million U.S. dollars. The pending case has not been broken.
July 18, 2016:
Taiwan’s “United Daily News†reported that the investigation bureau’s security personnel in New Taipei City had found malicious programs to invade the headquarters in Taiwan through a bank branch in London, UK. The police have interviewed three people, including the Head of Information at the First Bank's London Branch, the head of the Taiwan Bank's Information Department at the First Bank, and the representatives of the ATM vendor's headquarters, in order to ascertain whether or not the ghost has been involved in the robbery. At the press conference held at 10 o'clock that night, the New Taipei City Bureau of Investigation pointed out that the update of the ATM machine program of the First Bank was automatically delivered to the ATMs by the internal host and server. On July 4, the intruder counterfeited the update software and sent it to the ATMs of the first bank to open the ATM remote control service (Telnet Service). Until July 9, the intruder logged in remotely, uploaded the ATM control program, and executed a test-dispensing switch. After the success of the “money eavesdropping†test, the behind-the-scenes controllers who had hid abroad began to issue large-scale remote control to dispense money. The money will be collected by each of you. After completing the robbery, the remote controller then clears all hidden control programs, record files, and execution documents. The investigators also gave the flow chart of the first bank being attacked , as follows:
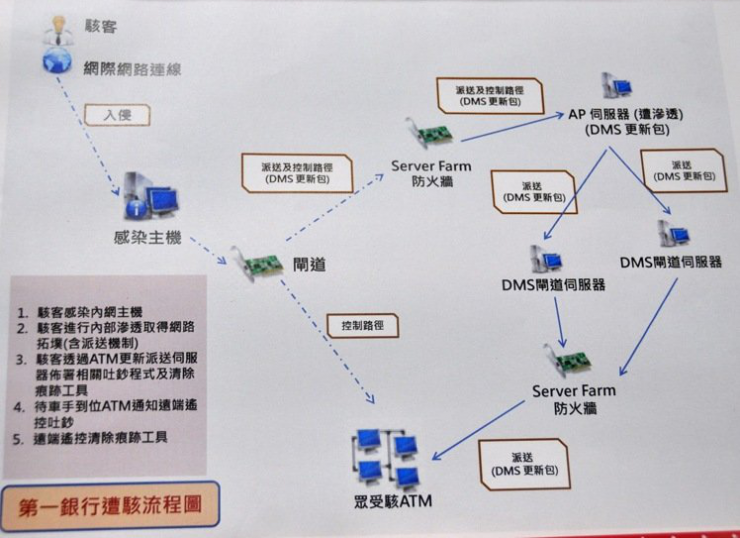
At the same time, the investigators found that the malicious program issued by the first bank ATM to issue a banknote was actually a computer from the first bank's London branch and two hard disk recorders, one of which had been damaged. Initially, the criminal group first entered the recording hard drive, obtained the highest authority of the computer host, and then implanted malicious programs in the ATM hard drive, and then sent foreign suspects to Taiwan to steal cash. The investigators suspect that the stolen consortium is likely to have other accomplices in London and does not rule out the possibility of being a ghost in the first bank.
July 20, 2016:
The Taipei City Police confirmed that it had found 12.23 million in cash in the mountains of Neihu. Andrew arrived at West Lake Park on the night of the 14th, but he waited for no one day to withdraw money, so he kept the cash in the garbage dump. The Taipei police finally found the cash by restoring Andrew's trajectory. An old man in the morning exercise picked up a computer bag with 4.54 million yuan in a parking lot near the West Lake Park. He took the money home and reported to the police in the evening. As of the 21st, about 5.86 million baht remained unclear, excluding the suspect’s living expenses.
| Event AnalysisOn the evening of July 12, the investigation department of New Taipei City released the information related to the malicious code that attacked the first bank: file name, MD5, and a brief description of the function. The sdelete.exe program is a normal trusted program provided by Microsoft.

In the analysis of relevant attack events, the 360 ​​team found that the attacker did not use bank cards and ATM operations, and did not need physical contact with the ATM. This enabled the ATM to dispense cash to achieve cash withdrawal. This point of attack has attracted our attention. Previous incidents of attacking ATMs are not uncommon, but it is relatively rare to be able to dispense ATM bills without making physical contact, although many researchers have proposed and verified this for years. theory.
On July 28, 2010, at the Black Hat Conference, Barnaby Jack, who was at IOActive at the time, presented his research results on ATM machine code over the years. He successfully demonstrated the intrusion of ATM machines installed with two different systems and gave the ATM on the spot. The cash machine spits money and he calls it "jackpotting." At the scene, he used two methods to make ATM machines spit out bills, one that required physical contact with the ATM, and the other that performed automatic attacks completely remotely. Both methods require malware to infect the machine system to execute false instructions from the attacker. The specific method is as follows:
l Physical Contact Attacks: Attackers make full use of the right to use the target machine, insert a special U disk, and then use the malware to control the network and instruct the machine to dispense money.
l Remote attack: An attacker uses a vulnerability in a remote management system to install malicious software. In most cases, it uses the remote administrator's default administrator password, account PIN, and TCP port. Then execute the malware and ATM will spit a certain amount of cash.
This phenomenon reminded us of the previously discovered Anunak (ie Carbanak) attack organization, which also achieved the same effect when attacking ATMs. Further, we analyzed the Anunak (ie Carbanak) and Taiwan First Bank events and compared them. There are more similarities among the people, as shown in the following table:
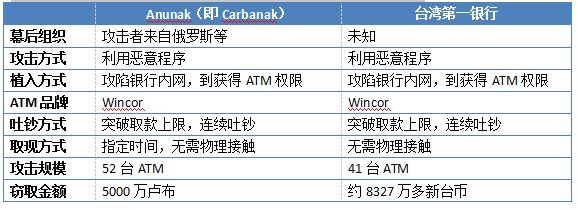
About Anunak (ie Carbanak):
The Anunak (ie Carbanak) attack organization is a multinational cybercrime gang. Since 2013, the criminal gang has launched attacks against 100 banks, electronic payment systems, and other financial institutions in about 30 countries and regions around the world. Currently, the relevant attacks are still active. In the “2015 China Advanced Persistent Threat (APT) Research Report†we mentioned Anunak. Through research and analysis of the organization’s relevant attack techniques and intentions, we consider the organization as criminal APT organization for the financial industry.
The Anunak organization generally attacks the computers of financial institution employees through social engineering, exploits, and other methods, and then invades the banking network. The attacker further monitors the computer through the internal network to view and record the screen of the bank employee responsible for the money transfer system. In this way, the attacker can learn the full details of the work of the bank's employees, imitating the behavior of bank employees and stealing funds and cash.
In addition, the organization can also control and operate the bank's ATM machines and order these machines to spit cash at designated times. When it is time to pay, the organization will send people to wait next to the ATM machine to take away cash that the machine "proactively" spit.
Threat to ATMTraditional threat
The traditional threats described here mainly refer to situations that do not use network attacks. As shown in the figure below, the traditional threats to ATM are mainly divided into these aspects.
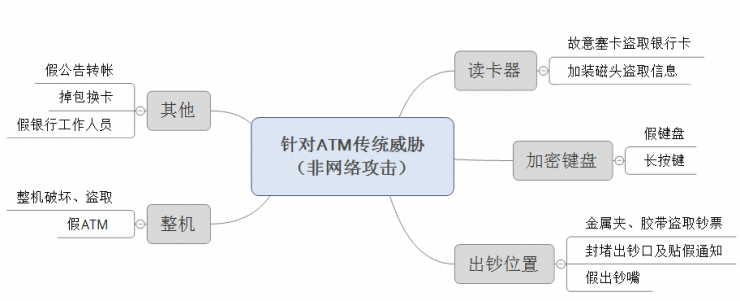
1, card replication is the main issue of ATM security
ATM crimes, such as the card number and other information that are stolen through card replicating devices, have long been known. On a global scale, the annual economic loss due to card replication amounts to 2.4 billion U.S. dollars. A common method used by criminals is to install illegal devices on the ATM to read the magnetic stripe information.
2. Increase in software attacks and external destruction
Software attacks against ATM include logical attacks, black box data attacks, and so on. ATM generally adopts the Windows open platform. Criminals can upload malicious software to ATMs easily via CD-ROM or USB, thus controlling cash out orders offline, causing huge cash risks. Other ways of committing crime include criminals opening the cabinet door on the ATM, using an electronic device to replace the ATM's IPC, linking to the ATM's cash withdrawal module, and then sending a non-authorized command to the cash dispensing module. Control ATM banknotes. The Times of Frauds survey shows that, since 2013, the number of logical attacks against ATMs is rapidly increasing and spreading worldwide. According to NCR Secure Fraud Net statistics, the number of physical attacks in global ATM cases has increased by 429% in the past few years
Use cyber attacks1, malicious programs
In cyberattacks for ATMs, it is mainly the use of malicious programs for subsequent attacks. How to implant malicious code is a key issue. First of all, through the invasion of the bank's internal network, access to ATM internal network permissions to further install the implant, the other is directly through the operation of the ATM itself, such as from the optical drive, USB and other attacks. The purpose of the related malicious program attacks is basically to make ATMs to dispense money under the control of an attacker, and some malicious programs also have the ability to collect data information such as bank cards.
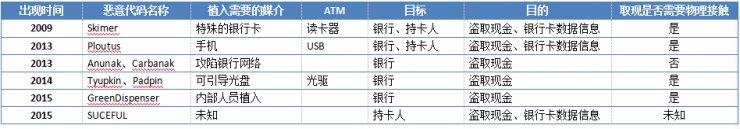
2. Information theft
It is generally an attacker who directly attacks banks or other financial institutions themselves, or uses other methods to obtain cardholder information (eg, name, card number, ID number, etc.). The data breach of the Standard Bank in this year has led to the theft of 1,400 ATMs in Japan, which is a typical case.
According to reports from the media, on May 15, 2016, the leaked data of a cybercrime gang, the Standard Bank, produced fake credit cards, taking 1.44 billion yen from ATMs at 1,400 convenience stores in Japan. The security measures of the shop are not enough, and these ATMs can accept foreign credit cards, allowing criminals to succeed.
Information disclosed by the police showed that the hackers’ actions were clearly planned. In the early morning of May 15, about 100 suspects in 16 districts and counties in Japan operated a total of 14,000 cash withdrawal instructions in 1600 hours. A credit card, where the highest cash withdrawal operation reached $913.
The South African Standard Bank has stated that it will bear all the financial losses caused by this hacking, and the cardholder will not be able to recover payment for the repayment. This information disclosure incident has already caused USD 19,250,000 in losses to the Standard Bank and may further in the future. increase.
3, the target of the attack
From the perspective of traditional threats to ATMs, the basic goal is to target cardholders and eventually lead to theft of property on the cardholder’s own account. In cyberattacks for ATMs, the ultimate goal is to attack cardholders by attacking cyberattacks. For example, copying bankcards through relevant information leads to money theft. The other is to attack the banks themselves and steal money directly from ATMs, such as the Taiwan First Bank Incident and the Anunak attacks related bank incidents.
We have also discovered that cybercrime activities in the financial industry have begun to evolve into a completely new stage. Malicious attackers have gradually shifted from targeting ordinary cardholders or ordinary users to targeting financial institutions such as banks. The purpose is to directly steal the bank’s own property.
Other threats to the banking system
In the attacks targeting the financial institutions themselves, especially the banking sector, in addition to targeting ATMs, the bank’s SWIFT system will be exposed. After the Bangladesh Central Bank was attacked by hackers in February 2016, it led to the theft of 81 million US dollars, such as the Vietnam Pioneer. Banks, Ecuadorian banks, etc., and other cyber attacks against the bank's SWIFT system were publicized one by one.
After the related events were exposed, we conducted an in-depth analysis of the tactical and technical aspects of the relevant attack incidents. We believe that the recent four bank-related attacks are not isolated, but are likely to be one or more organizations. Organize coordinated launches of different attacks.
In addition, Anunak organized attacks against the bank's SWIFT system in related attacks, but we analyzed its attack tactics and found that its behind-the-scenes organization and attacks on the Central Bank of Bangladesh should not be an organization.
About SWIFT:
SWIFT stands for Society for Worldwide Interbank Financial Telecommunication. The Chinese name is "Global Banking Financial Telecommunication Association". In May 1973, SWIFT was officially established by major banks in the United States, Canada, and Europe. Its headquarters is in Brussels, Belgium. It is a non-profit established to solve the problem that financial communications in various countries cannot adapt to the rapid growth of international payment and liquidation. The organization responsible for the design, establishment and management of the SWIFT international network for the transmission and routing of international financial information between members of the organization.
to sum upThrough in-depth follow-up and analysis of Taiwan's First Bank Incident, the Central Bank of Bangladesh and other incidents, we have discovered that cyber attacks against the financial industry have begun to evolve. Attackers are not limited to ordinary end-users but gradually target financial institutions themselves.
In addition, these attacks against the financial institutions such as banks and their attack methods are APT organizations or use APT attacks. This shows that the APT organization started its business-oriented attacks and used APT methods to conduct business-related attacks.
From the perspective of the financial industry security incident in the first half of this year, financial related industries such as banks have exposed many security issues. With the deepening of the investigation, the process of attack on the first bank in Taiwan has gradually become clear, but there are still many details that have not yet been publicly explained. However, regardless of whether the relevant personnel work negligently suffered from hacking attacks or there are insiders assisting the attacker, the attacker uses the telephone recording from the London branch to invade the ATM machine at the station to inject the malicious program, and the next instruction tells money, and every link is Financial security is closely related. Although the Taiwan ATM theft case has recovered most of the money and arrested some of the suspects, it cannot be overlooked that the first bank’s system has serious security problems.
Some security suggestions about ATM:
1, upgrade the operating system
2. Provide as complete physical protection and installation monitoring as possible
3, lock the BIOS to prevent boot from unauthorized media, such as bootable CD or U disk
4, reset the ATM machine all locks and master passwords, deny the machine comes with the default settings and password
5. Ensure that the anti-virus solution or software protecting the ATM is up-to-date
Lei Feng network press: This article comes from 360 security guards (Enterprise), FreeBuf hackers and geeks (FreeBuf.COM) released Lei Feng network, reproduced, please retain the source and author, not to delete the content.